PostHog's access control system lets you manage permissions across three levels: organizations, projects, and resources. This hierarchical approach provides granular control over who can view and edit different parts of PostHog.
Three levels of access control
1. Organization level
Organization members have one of three access levels that determine their permissions for organization-wide settings and actions.
There are three access levels in PostHog: Member, Admin, and Owner. An organization must have at lest one Owner.
| Permission | Member (base level) | Admin | Owner |
|---|---|---|---|
| Viewing and querying project data | ✔ | ✔ | ✔ |
| Accessing billing management | ✖ | ✔ | ✔ |
| Managing reverse proxies | ✖ | ✔ | ✔ |
| Creating and deleting projects | ✖ | ✔ | ✔ |
| Managing project access controls (see more below) | ✖ | ✔ | ✔ |
| Changing authentication settings (SAML, SSO settings, 2FA enforcement, etc.) | ✖ | ✔ | ✔ |
| Changing organization settings (name, logo, etc.) | ✖ | ✔ | ✔ |
| Managing RBAC Roles (creating, editing, deleting, changing members, etc.) | ✖ | ✔ | ✔ |
| Inviting new members (only for current level or below) | ✔ | ✔ | ✔ |
| Managing members (changing roles, removing, etc.) | ✖ | ✔ | ✔ |
| Leaving an organization | ✔ | ✔ | ✖ |
| Transferring organization ownership | ✖ | ✖ | ✔ |
| Deleting an organization | ✖ | ✖ | ✔ |
Access levels can be viewed and changed in the Members section of organization settings.
2. Project level
This is currently being rolled out to all users so you may not see this experience yet. If you're interested in trying it out please email zach@posthog.com with "Access control beta" in the subject line.
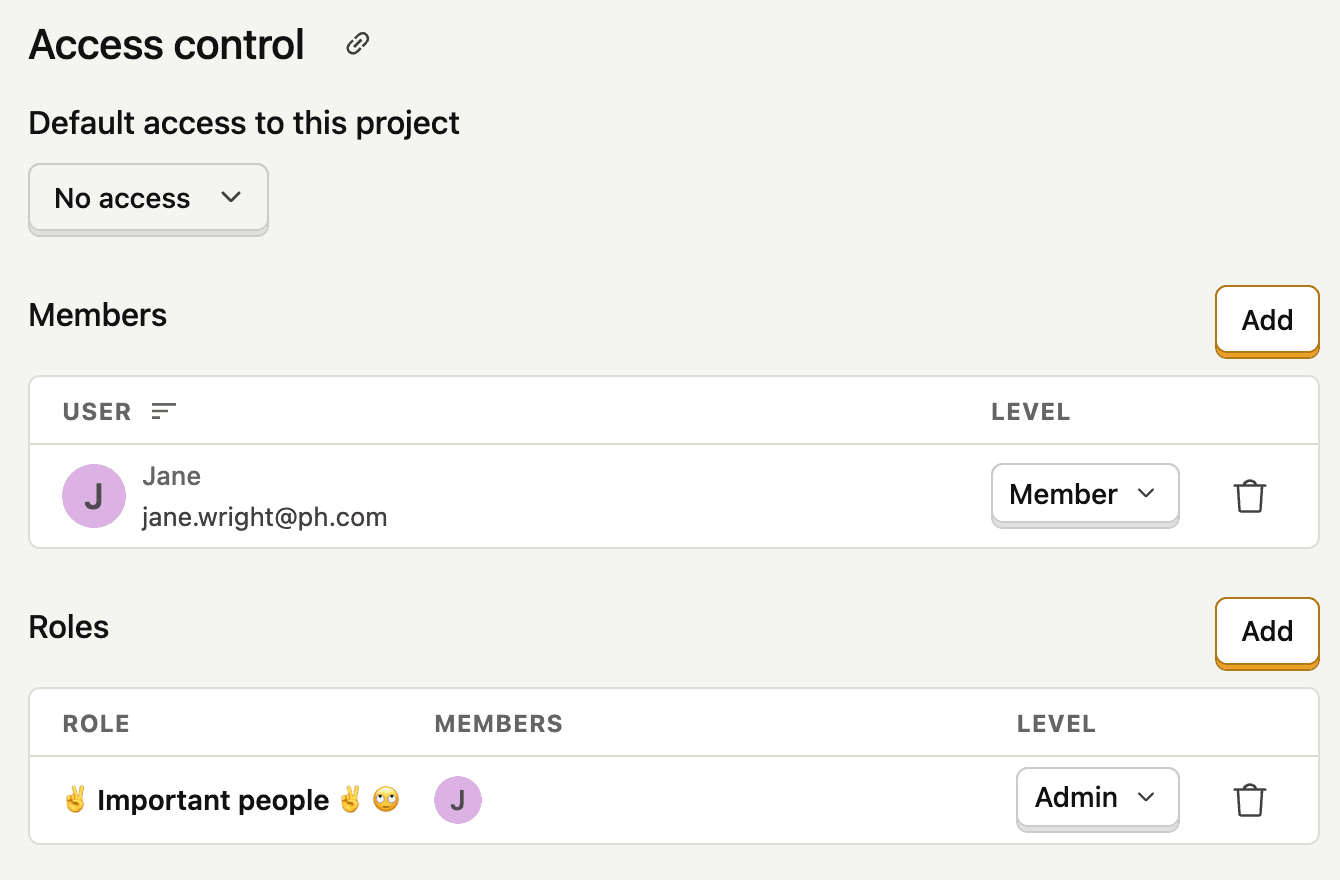
Each project has a default access level that applies to all organization members:
- No access - Members need explicit permission to access the project
- Member - All organization members have member-level access
- Admin - All organization members have admin-level access
Project permissions:
- Members can view and edit resources they create or are explicitly given access to
- Admins can view and edit all resources and manage access control settings
Organization owners and admins automatically receive project admin permissions.
You can override the default access level for specific members or roles. A user's effective permission is the highest level granted across all sources.
3. Resource level
This is currently being rolled out to all users so you may not see this experience yet. If you're interested in trying it out please email zach@posthog.com with "Access control beta" in the subject line.
Access control is available for:
- Insights
- Dashboards
- Notebooks
- Feature flags
- (more resource types coming soon)
Each resource has three possible access levels:
- No access - Cannot view or edit the resource
- View - Can view but not modify the resource
- Edit - Can view and modify the resource
Resources default to "Edit" access when created. You can modify the default and set specific permissions for members and roles.
Resource creators and project admins can always view and edit resources as well as manage access controls.
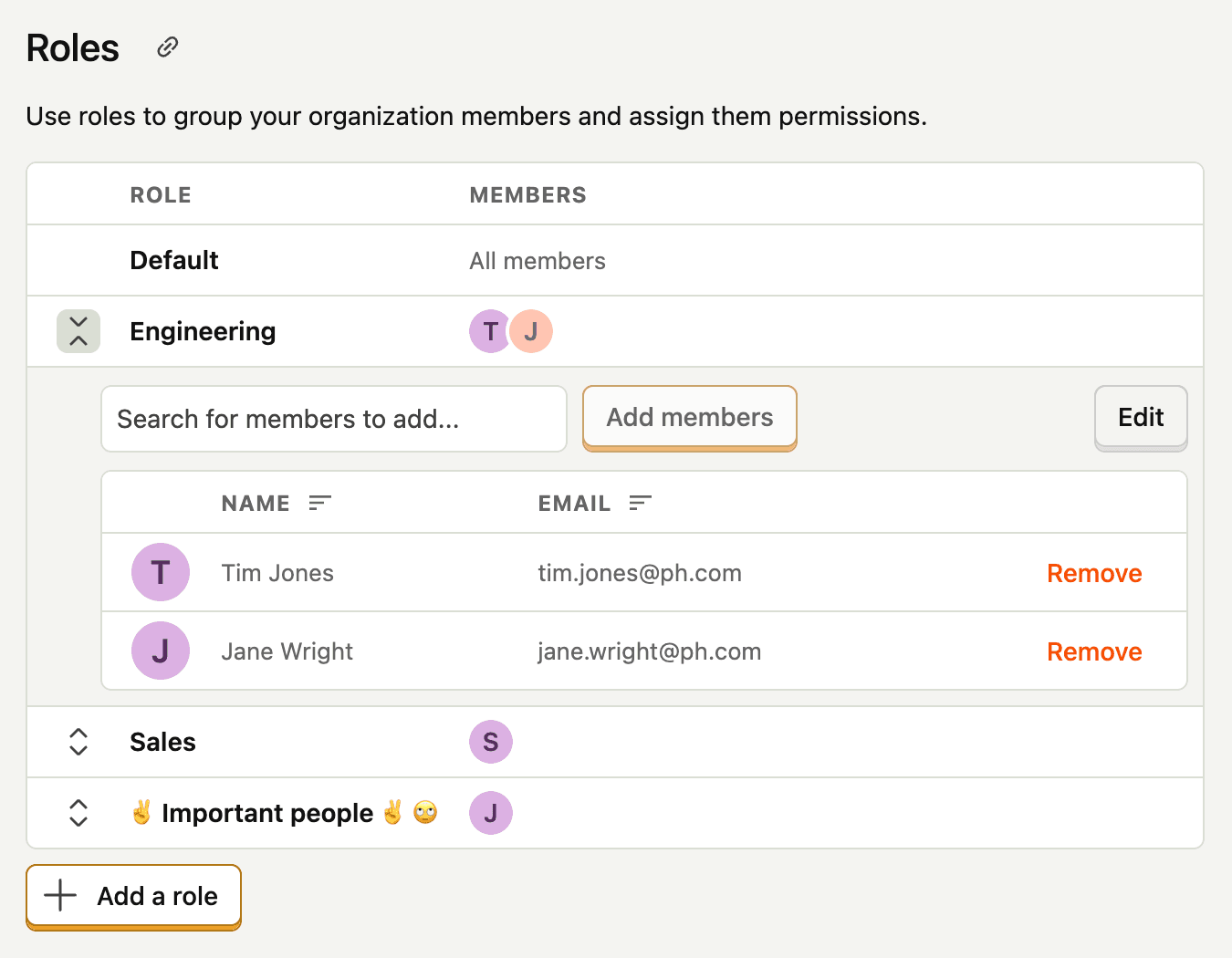
Role-based access control (RBAC)
RBAC is only available on Enterprise plans
Instead of managing permissions individually, you can create roles to group users together. Roles can be assigned permissions at both the project and resource level.
Feature availability
The Teams Add-on includes "Advanced Permissions" - the ability to set default access levels and member-specific access levels for projects and resources.
Enterprise adds role-based access control for managing access for groups of organization members.
| Feature | Free | Teams | Enterprise |
|---|---|---|---|
| Organization access levels | ✔ | ✔ | ✔ |
| Project access control (default and member-specific) | ✖ | ✔ | ✔ |
| Resource access control (default and member-specific) | ✖ | ✔ | ✔ |
| Role-based access control (for projects and resources) | ✖ | ✖ | ✔ |